Data Communication
SECTION A
Question 1
Part (a)
The steps of TLS Handshake Protocol are as follows:
- - Hello messages are exchanged to agree on the algorithms to use, random value exchange, and checking for the resumption of the session
- - Rrequired cryptographic parameters are exchanged to allow an agreement between the client and server on the key-exchange method and the premaster secret.
- - Certificates are exchanged and verified and the cryptographic information also exchanged for authentication of the client and server.
- - The master secret is generated from the exchanged random values and the premaster secret
- - The security parameters are then provided to the record layer.
- - A handshake is confirmed to have occurred without tampering from a possible attacker by verification of same security parameter calculations from the client and server.
The TLS protocol is shown in the figure below.
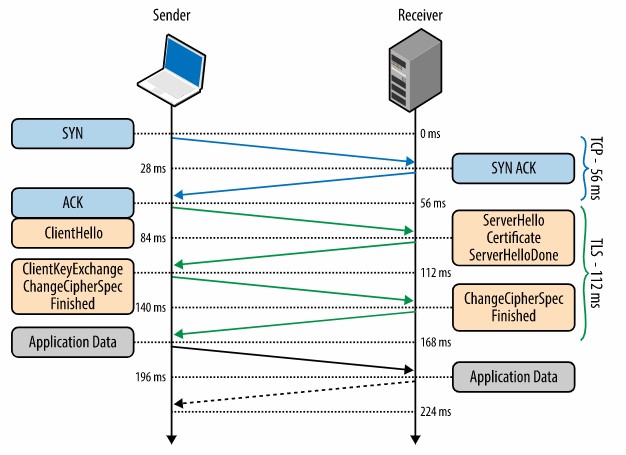
Figure 1.1: The TLS Protocol (adapted from https://hpbn.co/transport-layer-security-tls/)
Before exchanging data over TLS protocol between the client and the server, the negotiation of the encrypted tunnel must be initiated. The cipher-suites are chosen, the certificates are verified and the client and the server agrees on the version of TLS Protocol to use. At 0 ms, the TLS protocol runs over a reliable TCP transport protocol to first complete the three-way TCP hand-shake. At 56 ms, the client sends a plain text with specifications. At 84 ms, the version of TLS protocol is picked by the server and also decides on the cipher-suite depending on the client’s specifications. At 112 ms, the client initiated a key-exchange method to establish the session’s symmetric key/ master secret. At 140 ms, the serve processes the parameters of the key-exchange method used from client to generate an encrypted finished message. Finally at 168 ms, the client decrypts the message using the symmetric key and a tunnel is established for data transmission.
Part (b)
In the context of TLS key exchange, the master secret is a 48 bytes symmetric key used for encryption between the Protocol Client and the Protocol server. The premaster secret is converted into master secret using the same algorithms in all the key-exchange methods and then the premaster secret is deleted from memory after the conversion. The premaster secret length depends on the key-exchange method used.
The Master secret is securely communicated using clever pseudorandom function (PRF) which combines the Master secret and seed data which is given to it.
Part (c)
The certificate is a TLS/SSL certificate called QuoVadis Certificate.
Created on 13/01/2020
Expires on 13/01/2022
The certificate was issued by QuoVadis EV SSL ICA G3 which is the Kingston’s Certificate Authority.
The CA was chosen since they prove the website user’s identity to a remote computer and ensures the identity of a remote computer is known.
SECTION B
Question 2
Part (a)
In digital communication, Phase Shift Keying (PSK) is a modulation technique where the carrier signal’s phase is altered (shifted) by varying a sinusoidal input at a particular time. Depending on the phases where the signal is shifted, PSK can either be Binary PSK (BPSK) or Quadrature PSK (QPSK). In BPSK, the carrier signal takes only two phase reversals/changes (at 00 and at 1800). In QPSK, the carrier signal takes four phase reversals/changes (at 00, at 900, at 1800 and at 2700). The figure below shows BPSK modulated output.
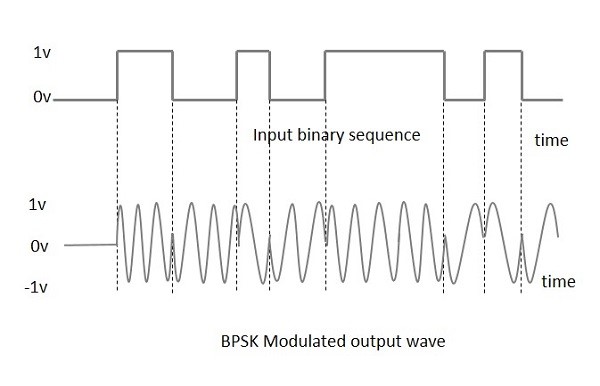
Figure 2.1: Adapted from https://www.tutorialspoint.com/digital_communication/digital_communication_phase_shift_keying.htm
Quadrature Amplitude Modulation (QAM) is a combination of PSK and amplitude shift keying (ASK) thus utilizes both analog and digital modulation concepts. QAM is done by changing both the phase and amplitude of the carrier signal being modulated. In QAM, two carrier signals are shifted in phase by 900 and then amplitude modulated thus causing variations in both amplitude and phase. The following figures shows the inputs and output of QAM modulator.
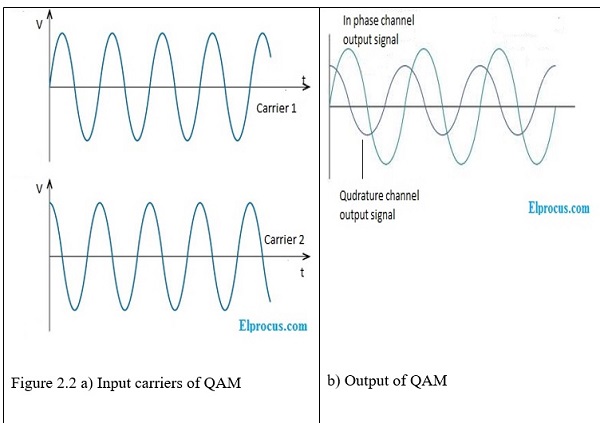
Adapted from https://www.elprocus.com/quadrature-amplitude-modulation/
Difference between PSK and QAM
PSK is a digital modulation scheme that depend mainly on assigning (mapping) each symbol (one or more bits) to a phase in 2-D space formed by In-phase (I) and Quadrature (Q) components. However , QAM utilizes both analog and digital modulation concepts to add an extra dimension other than (I) and (Q), that is, amplitude, to give more flexibility without increasing number of phases.
Part (b)
Consider the constellation scatter-diagrams below generated by SIMULINK for the following discussions on the performance of PSK and rectangular QAM.
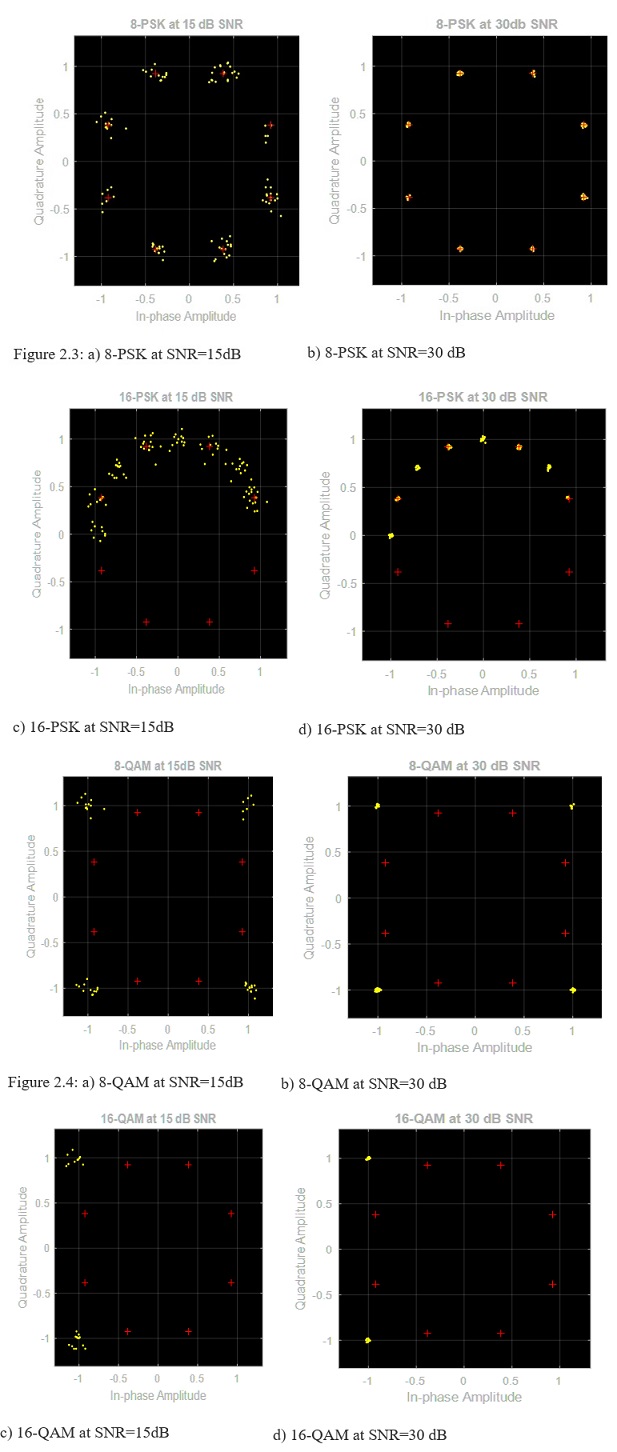
Comparing the 8-PSK and 8-QAM at a signal to noise ratio of 15 dB, it is noted that the 8-QAM has a lower Bit Error Rate (BER) and Symbol Error Rate (SER) than that of 8-PSK. This is due to the reduction of Euclidean distance between two adjacent constellation points in QAM.
It is noted that increasing number of phases to 16-PSK and 16-QAM at the same SNR makes the signal exposed to large BER and SER since increasing the alphabet size, M of the symbols makes Euclidean distance between consecutive symbols larger.
However, increasing the SNR from 15dB to 30dB reduced the BER and SER for both the PSK and QAM schemes.
The SIMULINK model used is shown in the figure below
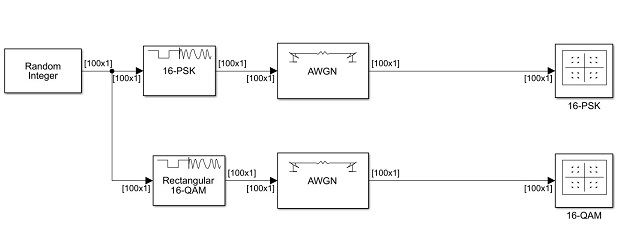
Figure 2.5: SIMULINK Model
Using a random integer as the input, the PSK and rectangular QAM modulation schemes are compared for performance. The symbols size is changed in the respective modulator blocks while the SNR is changed in the AWGN block which is used to introduce white noise.
Part (c)
PSK and QAM are widely used modulation techniques in digital communication for applications such as advanced wireless networks (Wi-Fi standards). The high spectral efficiencies of the modulation schemes for wireless networks applications is achieved by setting a suitable constellation size as discussed in part (b) above to limit the noise level and thus ensures that the communication channels is linear.
High bit rate QAM such as 16-QAM and 64-QAM are used in optical fiber systems since they can be emulated optically using a 3-path interferometer.
SECTION C
Question 4
Part (a)
What happens when we enter a website in the browser?
Firstly, when you enter the URL to the web browser, the web browser will lookup for the IP address of the domain name that was entered with the help of the DNS service which is being used in this case.
After that, the browser will send the HTTP request to the server and wait for the request to get a response. Once the response is received by the server we will get back the HTTP response.
As soon as the response is registered then the browser will begin rendering the HTML tags and the page will start loading automatically. After which the browser will send the request for adding additional objects that are being embedded with the HTML such as CSS, Javascript, Graphics, etc.
The browser will repeatedly get the response for all the requests made once all the requests are being made then the page will be stopped for loading and will be displayed to the user accordingly.
Once the browser has stopped completely loading then the browser will send more of the requests for async as per the requirement of the browser.
Hence, these are the steps that happen when we try to view the webpage using the browser.
Part (b)
Real-Time Streaming Protocol (RTSP) is used for transmission of real time data like audio and videos. It is designed for use in communication systems to control streaming media servers.
- HTTP friendly: It makes uses of HTTP concepts wherever possible
- Ease for parse: HTML or MIME parser can be made use in real time streaming protocol
- Scalability: New parameters or methods can be easily added in the protocol
- Firewall friendly: Both application and transport layer firewalls can be easily handled with means of protocol
- RTSP provides bi-directionality enabling full stream mode.
Part (c)
Generally,
Time of propagation,t=(distance,d)/(propagation speed,s)
t=d/s
The propagation delay is independent of the packet length, L and also independent of the transmission rate, R used to transmit the data.
Here;
distance,d=2500 Km=2500×103 m
propagation speed,s=2.5 ×108 m/s
t=(2500 ×103 )/(2.5 ×108 )=0.01 seconds
t=0.01 s
In CSMA/CD, the propagation delay ensures that two packets do not collide in the channel. Collision makes the channel unutilized for the transmission duration/ time of the packets that collided. CSMA/CD reduces wastage of channel capacity by continuous monitoring of the channel via nodes during packet transmission to ensure that the transmission stops when a collision between packets is detected.
Buy Data Communication Answers Online
Talk to our expert to get the help with Data Communication to complete your assessment on time and boost your grades now
The main aim/motive of the management assignment help services is to get connect with a greater number of students, and effectively help, and support them in getting completing their assignments the students also get find this a wonderful opportunity where they could effectively learn more about their topics, as the experts also have the best team members with them in which all the members effectively support each other to get complete their diploma assignments. They complete the assessments of the students in an appropriate manner and deliver them back to the students before the due date of the assignment so that the students could timely submit this, and can score higher marks. The experts of the assignment help services at urgenthomework.com are so much skilled, capable, talented, and experienced in their field of programming homework help writing assignments, so, for this, they can effectively write the best economics assignment help services.

