Network Design Assessment Item 2
Executive Summary
In designing a network, the company Smart Pharmacy is considered where it specializes in working for both international and national franchise clients based in Australia. The company is established in Botany, NSW Australia, through supplying medical services to worldwide franchises. By utilizing the top down approach of the network design, Smart Pharmacy has made an identical network design, which can address the technical and business goals, it provides proper security, user-friendly design and solutions without cloud intervenes.
Moreover, the report provides a detailed section regarding the project testing and planning utilizing the top down approach the project scope and goals have also been stated. A logical and physical diagram of the network has been provided which describes all about the location of devices along with security techniques. The DMZ zone for the servers that has been implemented is installed for isolating those devices from external vulnerabilities. Therefore, the tables of hardware requirements have also been provided along with explanation of its uses. At the end of the report, it has discussed about the routing and switching protocols along with testing plan and scripts.
Goal of the project
Designing network architecture for a corporate organization with diverse application, end-user device and user community mix is a complex task for majority of the networking teams. In this project its goal is to develop a secure network design of Smart Pharmacy in Australia. The report will be explaining the project regarding network topology of the organization and the number of equipment required in making the project. Utilizing the top down approach the design of the network will be followed to provide a cost effective solution in a efficient way between the franchise clients and the company
Scope of the project
The project scope is the portion of the project that involves in documenting the list of cost, functions, features, deadlines of specific goals. The project scope for the Smart pharmacy includes the design of the network utilizing the top down methodology such that it can provide an efficient and cost effective solution to business.
The design of the network requires communicating with the medicine delivery persons by locations tracking and distributing the order information that requires to be delivered to the patients at their home. The order confirmation will be done by the franchise clients by viewing the inventory stocks before delivery.
The scope is also to accomplish the goals of business like providing better products, services at affordable costs and in effective way. The technical goals concern about the protection of franchise clients and data of sales along with making a highly secured design of network, which can communicate the delivery persons and vehicles at Botany, NSW office. It allows the customers to check the orders for offering endorsement through online system.
The scope of the proposed project and its limitations will not intervene solutions of cloud and missing data such as the number of vehicles, number of patients, number of clients and entire budget for the project and the availability percentage required.
Business goals and project constraints
Business goals
According to the provided case study, organizational goals of the business for Smart Pharmacy are 3 key goals and they are as follows:
- Smart Pharmacy and its first goal are to purchase its products from various manufacturers across the globe and will be delivering to each franchise at affordable cost in effective way and it can develop a better service to customers.
- The second goal is to deliver better price-oriented products to patients (Clement and Puranam 2018). It can accomplish by minimizing the delivery operation cost from nearest local medicine providers to the location of clients.
- The third goal is to provide a well efficient website where the patients or customers can browse through entire products of SP and selecting the franchise pharmacy and the products they will be capable of paying online and collect the products at chosen franchise.
- Another goal is the on-tracking of vehicles for delivery and on- viewing of orders to be permitted by the customers before providing by vehicles to customers or patients.
Business constraints
No solution based on cloud storage is the limitation of the project, which would enable modern technology for fewer investments associated to constraints of cost.
The data regarding budget of the project will be beneficial for the network design more accurately, which is missing in this context.
List of Technical Goals and Tradeoffs
Technical Goals
- Both for the sales and client, the security of data are required to be considered in the network design.
- The utilization of cloud solution is not inspired and thus the servers are required to be located at Botany, NSW offices physically with entire transactional data (Karmakar et al. 2020)
- A protected connection is between the Botany office and delivery vehicles required to be accomplished.
Tradeoffs
- Scalability is not required for the current business, but it can be acknowledged that the industry could enhance its growth in the future.
- Around 95% availability could be accomplished depending on the design of Smart Pharmacy network.
- The performance will increase, as the response time for server and entire communication of the devices for good score.
- One of the key concerns of the business goals is security of the sales and client’s sensitive data (Evtodieva et al. 2016)
- The manageability for the network device and tools requires extra staffs for any type of physical issues
- As there are minimum software and hardware required, the affordability would be a good point for the business requirements.
- The usability will be considered at all user levels as a core function, if the organization is to focus on its requirements.
- Affordability: 20
- Adaptability: 5
- Usability: 5
- Manageability: 5
- Security: 15
- Network performance: 20
- Availability: 20
- Scalability: 10
Total: 100
Table of Data Stores, Network Applications, User Communities, and Traffic Flows
User Communities
Below table depicts the user communities and therefore, all of them are assumed:
|
Name of the User Community |
Community Size (Users Number) |
Location(s) of the Community |
Application(s) Used by Community |
|
MD (The managing director of SP) |
One |
Botany, NSW Office |
FTP server and Application server |
|
Accounts and Finance manager |
One |
Botany, NSW Office |
FTP server and Database server |
|
Logistics manger |
One |
Botany, NSW Office |
Application server. |
|
Purchasing manager |
One |
Botany, NSW Office |
FTP server and Database server |
|
Franchise (clients) |
60 (assumed number) |
Botany, NSW Office |
Webserver |
|
Storekeeper |
One |
Botany, NSW Office |
Webserver |
|
Deliveryman |
30 (approximately) |
Australia (Remote places) |
Webserver and IoT devices. |
Table 1: User communities
Data stores
|
Data Stores |
Location |
Application (s |
Used by User Community (or Communities) |
|
Webserver |
Botany, NSW Office |
Apache web server will be utilized for access to website in order to make transactions and live view of orders (Habibullah, Rondeau and Georges 2018) |
Purchasing manager |
|
Application server |
Botany, NSW Office |
For making automation to the business process |
MD Logistics manger |
|
Database |
Botany, NSW Office |
For storing client’s data and transactions |
Accounts and finance manager |
|
FTP Server |
Botany, NSW Office |
Cyberduck, Fillezilla |
MD Accountant Logistics manager |
|
DHCP server |
Botany, NSW Office |
Utilized for allocating IP address for all present devices |
Utilized by all inner devices of Smart Pharmacy |
Table 2: Data stores
Network Applications along with the Traffic Flows
|
Application name |
Type of Traffic Flow |
Protocols that are Utilized by Application |
User Communities that Utilize the Application |
Data Stores (Servers, Hosts, and others |
Estimated Requirement of Bandwidth |
QoS Requirements |
|
Automated application software |
Program software with automation and internal users ( Sheikh 2020) |
Un-reserved number of ports |
Logistics manager and MD |
Server |
2-4 Mbps |
It is to ensure that the automation process stores the transaction orders and associated data |
|
FileZilla (FTP application) |
Server to clients |
Cyberduck, Fillezilla |
Purchasing manager, Accounts manager and MD |
Server |
2-3 Mbps |
Locally upload and download the files |
|
ExpressVPN |
Clients to the servers |
IPsec protocol |
Storekeeper and delivery persons |
VPN server |
2-4 Mbps |
Requires to offer secured connections |
|
Apache Webserver |
Server to the browser of clients |
TCP port 433 https |
Logistics manager and delivery persons |
Record the web pages |
1-3 Mbps |
Requires to secure and ensure less network load delay |
|
DCHP server |
Server to client machines |
TCP port number 67 and 68. |
Entire devices in Smart Pharmacy network |
Configured DHCP Server |
2-3 Mbps |
NO conflicts in IP and minimize the work of admin |
Table 3: Network applications that are used along with the traffic flows
Justification and explaining the design of the logical network
The logical diagram provided in this section will consider the technical goals and the business, which has been developed using the top down approach. The assumptions have been made for the delivery vehicles, which are connected to the network using the cellular network by the Virtual Private Number (VPN). An enterprise server is utilized by SP only cannot be utilized by external users. The public access servers like DNS, FTP and webserver are secured in DMZ by separating the servers from inner network. Through filtering the malevolent traffic, the DMZ zone is protected by firewall.
On both the switches, the users are connected to the staff’s devices like to a standard printer, PC and a telephone. The below diagram is classified into access, distributed and core layer. It has the user community utilizing the network resources. Between the access and core layer, the distribution layer is present, which supports rapid communication between the departments and prevents a direct link from the core devices. Moreover, the DMZ servers are isolated from the network LAN as they are accessed publicly and thus it is made to isolate from its internal network in order to have a robust security. The enterprise server networks are utilized for internal means for the development of business and are utilized for only office purpose.
Moreover, there are two switches that are connected to users in order to avoid single point failure and therefore, the people share a standard office printer. Alongside, there is a telephone that will work utilizing voice over internet protocols.
The GPS enabled vehicles that are provided is made of assumption and it is ensured that every vehicle’s person will be utilizing the technology of VPN software according to requirement of SP.
Logical Network Diagram
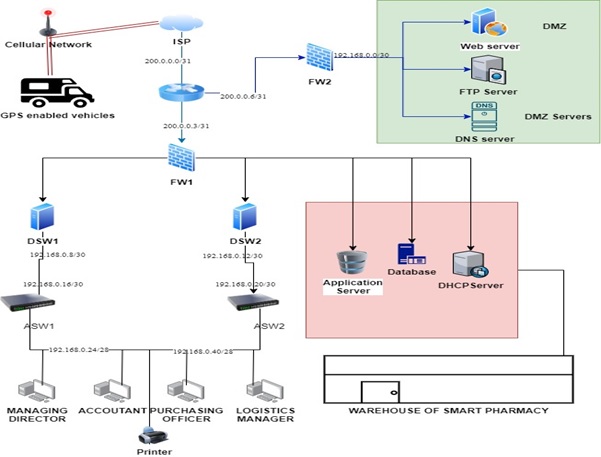
Figure: Logical Network diagram of SP
(Source: Created by Learner)
IP addressing scheme
|
Naming of network |
Subnets |
Ranges |
Address number |
|
ISP to Router |
200.0.0.0/31 |
200.0.0.1 |
2 |
|
Router to FW1 |
200.0.0.3/31 |
200.0.0.4 |
2 |
|
Router to FW2 (DMZ) |
200.0.0.6/31 |
200.0.0.7 |
2 |
|
DMZ Server to FW2 |
192.168.0.0/30 |
192.168.0.1 to 192.168.0.2 |
4 |
|
Enterprise Server to FW1 (firewall) |
192.168.0.4/30 |
192.168.0.5 to 192.168.0.6 |
4 |
|
FW1 to DSW1 (distribution switch) |
192.168.0.8/30 |
192.168.0.9 to 192.168.0.9 |
4 |
|
FW1 to DSW2 |
192.168.0.12/30 |
192.168.0.13 to 192.168.0.14 |
4 |
|
DW1 to ASW1and2 (Access switch) |
192.168.0.16/30 |
192.168.0.17 to 192.168.0.18/30 |
4 |
|
DW2 to ASW1and2 |
192.168.0.20/30 |
192.168.0.21 to 192.168.0.22 |
4 |
|
ASW1 to staffs |
192.168.0.24/28 |
192.168.0.25 to 192.168.0.38 |
16 |
|
ASW1 to staffs |
192.168.0.40/28 |
192.168.0.41 to 192.168.0.55 |
16 |
Table 4: IP addressing scheme of SP
(Source: Created by learner)
List of routing and switching protocols, and security mechanisms
Routing
|
Name of protocols |
Location of router |
|
OSPF |
Core R1 (LAN interior core layer network) |
|
STATIC |
FW1 (inner DMZ routers) |
|
BGP |
R1(external routers) |
Switching
|
Switching Protocol |
Location of switch |
|
Virtual LAN |
Sw1 and Sw2 |
|
STP (Spanning tree protocol) |
MSW1 and MSW2 (core layer) |
Security mechanisms
Smart Pharmacy has some security mechanism on its network layers referenced to OSI layers connection.
Physical layer
In this specific layer, the physical network cables that are connected are exposed to minimize and destroy the communication availability. Thus, to overcome this issue, the utilization of access cards and surveillance cameras in SP are required.
Data link layer
The switch and its protection are requiring through blocking the unutilized ports. So, a logical security by utilizing the protocol of WPA2 is needed for WLAN communications and thereafter, a VLAN can be utilized to isolate the user group utilizing the applications or the server
Network Layer
It is the core layer in the network design and is more likely to be attacked from external side. So a robust password utilizing suitable protocol configuration of VPN or ACL is needed.
Transport layer
The data encryption in this layer will be secured through developing authenticity by utilizing Secure socket layer to get the SSH and https in accessing the databases
Application layer
The DNS and Websewrver protection can be secured through utilizing high end firewalls, which can monitor the traffic by filtering it and thus make a good policy of protection.
Physical layer
At Botany, NSW office, a role based access will be provided to users that will provide a privilege and responsibility to them while accessing network data. Therefore, utilizing access cards will be needed for entering or exiting from office.
Physical network diagram
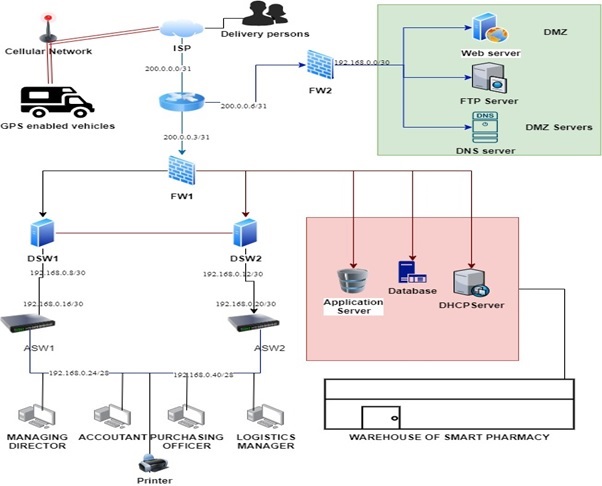
Figure 2: Physical diagram of SP
(Source: Created by learner)
Networking & communication devices and applications
|
Location devices |
Manufacturer and model |
Costs |
|
Router |
TP-Link Safestream Multi WAN VPN Router |
$600.00 |
|
Firewall |
Zyxel ZyWALL (USG) UTM Firewall, Gigabit Ports, 20 IPSec VPN, 5 SSL VPN |
$360.20 |
|
Switch |
NETGEAR 24-Port Gigabit Ethernet Unmanaged Switch (JGS524) |
$525.30 |
|
Servers |
Dell PowerEdge T40 Server, BTX Intel Xeon E-2224G 3.5GHz, 8GB 2666MT/s DDR4, 1TB 7.2K RPM SATA |
$13,455.00 |
|
Printer |
Canon TR8620 All-In-One Printer |
$2500.50 |
|
Telephone |
SP-6651-K10 |
$400.00 |
Justification of the networking & communication devices and applications required
Router: The selected router will be utilized to interact with VPN access and configure NAT.
Firewall: The inner network and DMZ can be secured to filter the user packets
Switches: The selected switch will be supporting the bandwidth for the flow of traffic across the network
Server: The selected server can be utilized for multiple user access and Virtual machines
Printer: The selected printer can deliver multiple jobs developed at single signal
Telephone: The selected telephone model is for SP and will be connected to internet access.
Test plan
|
Sl. No |
Requirements |
Typical components |
Description |
|
1. |
Introduction |
1. Test Approach |
The system network and its main objective are to protect the client and transactional data. |
|
2. Scope |
From external side of the enterprise, the network must not be accessed by public and thus there are certain particular servers that are kept isolated from the core network that are vulnerable to exterior threats (Dadheech, Choudhary and Bhatia, 2018) | ||
|
3. Assumptions |
The demilitarized (DMZ) zone is thus created for those servers. It has the DNS, mail and web server altogether. Depending on the utilization of resource the traffic can be relied on users. | ||
|
2 |
Static testing |
1. Improvements |
The objective is to test the confidential network areas that are in DMZ. It should be test with penetration testing to verify the network strength and security of before going to the phase of implementation. |
|
2. Standards |
The kali tools are utilized widely for the testing and for network security analysis. | ||
|
3. Developing the documentation standards |
It can be predefined about the acceptance criteria where it can be deciding that how firewall of DMZ blocks the undesired request of TCP (Iovan and Robu 2016). Documentation has been done accordingly. | ||
|
3 |
Dynamic testing |
1. Test data |
The test types can be analysing by implementing the test on the device types like webserver situated at the DMZ. |
|
2. Conditions |
The users can actually know about the load time duration and request response from the clients in order to make secure transactions (Bhardwa et al. 2016). | ||
|
3. Results |
Between 8AM to 5PM, the number of request of traffic during office hours is referred as peak time and there must not be any delay in webserver loading. | ||
|
4. Log status |
Generated successfully | ||
|
4 |
Environment |
1. Strategy |
Top-down approach |
|
2. Tools |
Cisco Packet Tracer | ||
|
3. Platform |
Network simulation | ||
|
4. Report |
Success |
Table: Testing plan
References
Bhardwaj, A., Subrahmanyam, G.V.B., Avasthi, V. and Sastry, H., 2016. Design a resilient network infrastructure security policy framework. Indian Journal of Science and Technology, 9(19), pp.1-8.
Clement, J. and Puranam, P., 2018. Searching for structure: Formal organization design as a guide to network evolution. Management Science, 64(8), pp.3879-3895.
Dadheech, K., Choudhary, A. and Bhatia, G., 2018, April. De-Militarized Zone: A Next Level to Network Security. In 2018 Second International Conference on Inventive Communication and Computational Technologies (ICICCT) (pp. 595-600). IEEE.
Evtodieva, T.E., Davydova, N.N., Videneeva, S.V. and Fedorov, V.A., 2016. The Concept of Network Organization and Design of Networks in Logistics. International Journal of Economic Perspectives, 10(3).
Habibullah, K.M., Rondeau, E. and Georges, J.P., 2018. Reducing energy consumption of network infrastructure using spectral approach. In Technology for Smart Futures (pp. 235-250). Springer, Cham.
Iovan, A. and Robu, R., 2016, February. Handling of the demilitarized zone using service providers in SAP. In IOP Conference Series: Materials Science and Engineering (Vol. 106, No. 1, p. 012003).
Karmakar, K.K., Varadharajan, V., Tupakula, U., Nepal, S. and Thapa, C., 2020, June. Towards a Security Enhanced Virtualised Network Infrastructure for Internet of Medical Things (IoMT). In 2020 6th IEEE Conference on Network Softwarization (NetSoft) (pp. 257-261). IEEE.
Sheikh, A.F., 2020. Network Fundamentals and Infrastructure Security. In CompTIA Security+ Certification Study Guide (pp. 9-34). Apress, Berkeley, CA.Network Fundamentals and Infrastructure Security. In CompTIA Security+ Certification Study Guide (pp. 9-34). Apress, Berkeley, CA.
Resources
- 24 x 7 Availability.
- Trained and Certified Experts.
- Deadline Guaranteed.
- Plagiarism Free.
- Privacy Guaranteed.
- Free download.
- Online help for all project.
- Homework Help Services

