IT 725 Network Technology Assignment 2
CS 725/825 Computer Networks, IT 725 Network Technology
Problems:
(10 points)
- What is the range of IP addresses covered by prefix 132.177.12.192/28?
- Give the prefix(es) to cover the IP address range 10.20.30.0 - 10.20.37.255.
- What is the netmask that corresponds to /11 prefix length?
- What prefix length corresponds to netmask 255.255.224.0? K. (10 points) Find two distinct command-line commands to:
- list all network interfaces of a host
- for each active network interface, find its IP address, hostname, subnet id, prefix, and subnet mask,
- list the content of the routing table and the default gateway, and
- list the content of the ARP table.
The easiest way is to try on two distinct platforms. Some platforms provide more than one way to answer the questions above, it is fine to give those.
(10 points) Use the dig command to emulate name resolution of gitlab.cs.unh.edu performed by someone outside of UNH, i.e., query one of the root name servers, get a list of TLD name servers for .edu TLD, query one of those, get a list of UNH name servers, query those to get the addresses of CS name servers, and, finally ask one of those for the IP address. Remember that the command option @<IP address> allows you to select a specific name server. Option +norecurse prevents a name server from performing a recursive query (in this case, the only name server that would actually do that is the UNH name server). The authoritative list of root name serves (named.root) can be downloaded from https://www.iana.org/domains/root/files. There is an option of dig that will make it to perform all the steps in one go, you are not allowed to use it.
(20 points) In this part of the assignment, you will analyze a brief trace of network traffic. The trace (https://www.cloudshark.org/captures/99b00585eb98) is available through CloudShark service provided by QA Cafe, a Portsmouth company with many UNH-CS and IOL connections founded by UNH CS alumnus Joe McEachern. You can also download the trace from the site in a format that can be opened by any of the standard network traffic sniffers, such as Wireshark or command-line utility tcpdump.
Analyze a trace stored on CloudShark that captures packets generated as a result of executing a traceroute and answer the following questions:
- What was the entire command line that was used?
- What is the hostname of the machine where the command was executed?
- As precisely as you can, determine what the exact output of the traceroute command was, including numerical values.
- The last set of probes result in a different response than the ones for nodes at distance one and two. Why?
- (5 points) Can you find the country where IP address 133.245.183 is registered? Can you find the hostname that corresponds to it? Give the commands that you used. Do not probe the address with ping, traceroute, or any other scanning tool. The address was picked because it was a source of probes sent to a web server that I occasionally run on my laptop for testing.
- (5 points) This question should be done on agate or any other computer with IPv6 connectivity. Can you find an IPv6 address of com? This is not an exercise in using a search engine to find an answer. Show the command(s) that you used. Is there anything interesting that you see in the address?
Programming assignment:
- (40 points) The goal of this assignment is to write a pair of applications that allows you to measure the offset between the clocks on two systems connected over a network. The solution must take into an account the time it takes to propagate the messages from one system to another.
More specifically, as the client application is started, it notes of the current time t1, sends a request to the server, the server notes the time the request arrived t2, prepares the response, gets the time the response is ready to leave t3, and sends both t2 and t3 back to the browser as a JSON-encoded object. The client notes the arrival time of the response t4 and calculates the round trip time (RTT) as (t4 - t1) - (t3 - t2), and the clock offset as (t1 + RTT/2) - t2:
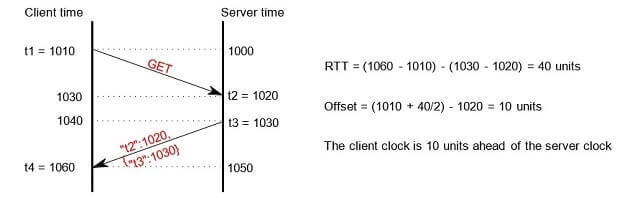
As you will see, your clock offset observation will differ slightly from run to run. This is a result of variable latencies in the underlying system. In order to get more precise results, your program must run the message exchange outlined above multiple times and use the multiple measurements to come up with a better estimate. How exactly you combine measurements is an open part of the assignment and should be outlined in the program report.
You are free to pick any underlying protocol for the message exchange as well as the programming language. You do have to carry out the final experiments between two different computers. However, it is perfectly fine to run both client and server on the same machine for initial testing (in that case, both use the same clock and your program should report an offset close to zero).
Deliverable
Just like in the previous assignment, write a brief report (two pages maximum, included in your single-file submission) that outlines the approach you took. There are two parts to the report. In the first one you will describe your approach. The second part of the report must show a representative run of your program together with appropriate explanations. Important: by showing an execution of your program, you are making a statement that your program, as submitted, works as shown. An attempt to "fake" a run, for example by writing a program that ignores input and just prints answers regardless of input, will be considered as cheating. Finally, remember, you may be asked to give a demo of your program. If your program does not implement fully the required functionality or does not work, you have to make it clear in the report.
The source code for the programming part of the assignment must be committed to your course Git repostory.

