COMP8270 Network System Design Assignment 1
Assignment Objectives
This assignment has been designed to test your knowledge in the following areas:
- Layer 2/3 switches
- Router architecture
- Interconnections
- Classification algorithms
Note
- Answers must be within the specified word limit. This is an absolute word limit and no excess will be allowed.
- Assumptions (if any) must be stated clearly in your answers.
Assignment Questions
-
In a Shared Memory Architecture, multiple processors can
read and write data from the same location.
Message Passing Architecture allows an alternate method for communication and movement of data among multiprocessors (compared to shared memory multiprocessor systems): There is no global memory so it provides a way to move data from one local memory to another by means of message passing.
With all other factors being constant, for the following programs, would a shared memory multiprocessor or a message-passing multiprocessor be a better choice?
- Values tend to be computed well in advance before they are used.
- The control structure is somewhat ambiguous, making it difficult to predict which data will be needed by each processor beforehand.{" "} (10 marks) (500 words)
- Most of the approaches to building a high speed router architecture recommend implementing the Address Resolution Protocol (ARP) functionality in the slow path. Cite and explain some reasons why this functionality should be in the fast path and not in the slow path.{" "} (5 marks) (300 words)
- When a layer 2 switch receives a broadcast packet, it floods the broadcast out on all its associated ports. This broadcast traffic can create congestion and bring the overall efficiency and performance of the network down. In such a situation, can the use of a Layer 3 switch help mitigate this problem to some extent?{" "} (5 marks) (200-250 words)
- A set of rules is shown in the table below. You are required to construct a Lucent Bit Vector data structure for this set of rules. You must use a bitmap of size 8 bits for characterizing the rules for classifying a packet with{" "} F1 = 0011 {" "} and{" "} F2 = 1111 . (5 marks)
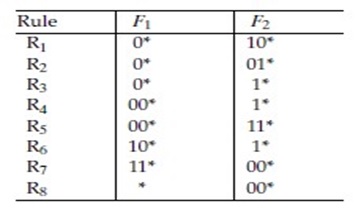
A 2- Field Classifier
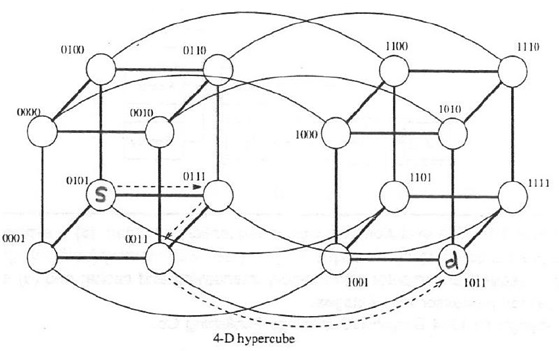
- Consider a 4-D hypercube network. Using the E-cube routing algorithm, show the sequence of steps to route messages from source node (0110) to destination node (1101). You must identify all the intermediate nodes on this routing path.{" "} (5 marks)
Submission
You must make an online submission on ilearn via Turnitin.
Assignments will normally be marked and returned online. There are no hardcopy submissions for written assignments.
Ensure you submit the correct file. The submission process shows you a complete preview of your entire assignment after you have uploaded it, but before you have submitted it. Carefully check through every single page to ensure everything is there and the correct version has been uploaded, and only then press CONFIRM.
Multiple submissions may be possible via Turnitin prior to the final due date and time of an assessment task and originality reports may be made available to students to view and check their levels of similarity prior to making a final submission. The first originality report will be available very soon after the initial submission to Turnitin but the subsequent originality reports require the passage of 24 hours before they are available after follow-up submissions. Students are encouraged to use these reports to ensure that they do not breach the Academic Honesty Policy through high levels of similarity (plagiarism).
Teaching staff will use the originality report to judge whether plagiarism has occurred and whether penalties should apply for breaches of the Academic Honesty Policy. Any similar text identified by Turnitin will be considered carefully to see if it is indeed a breach of the Academic Honesty Policy.
Note
- Answers must be within the specified word limit. This is an absolute word limit and no excess will be allowed.
- Assumptions (if any) must be stated clearly in your answers.
Remember, there may not be one right answer for some of the questions. Rather, your explanations do need to present your case clearly. The explanations you provide do not have to be long; a concise one is preferred to a rambling one.
Cyber Security Homework Help
- Ethical Hacking
- Networking Basics homework assignment help
- Inter process Communication/Threads homework assignment help
- Introduction, Framing homework assignment help
- Error Detection homework assignment help
- Flow Control, Reliability homework assignment help
- Wireless - 802.11 homework assignment help
- Wi-Fi Wireless homework assignment help
- DSL homework assignment help
- PACKET SWITCHING (Network Layer) homework assignment help
- Routing - Link State and homework assignment help
- Distance Vector homework assignment help
- ATM homework assignment help
- PROTOCOL homework assignment help
- Network Hardware homework assignment help
- Internet Connection homework assignment help
- TCP Extensions and homework assignment help
- Performance Enhancements homework assignment help
- TCP/IP Networking homework assignment help
- Bridge homework assignment help
- IPv4, IPv6, ICMP, ARP homework assignment help
- IP Routing - CIDR, OSPF homework assignment help
- Proxy Server / Lists homework assignment help
- Multicast homework assignment help
- DNS homework assignment help
- VPN homework assignment help
- CONGESTION CONTROL homework assignment help
- Congestion Avoidance homework assignment help
- peer to peer (P2P) homework assignment help
- Virtual Clock homework assignment help
- Windows Network homework assignment help
- Bluetooth homework assignment help
- Free Practice Test homework assignment help

